As the digital world continues to evolve, so does the need for improved cybersecurity measures. With new threats emerging every day, it’s essential for businesses, organizations and individuals to stay up-to-date with the latest trends. In this blog post, we’ll explore what is expected in terms of cybersecurity trends in 2023 and how you can best prepare yourself now.

Technology is always changing, and so are the security threats that come with it. Cybersecurity trends in 2023 will focus on the potential of artificial intelligence (AI), targeted ransomware attacks, user awareness, 5G speed and internet speeds, a privacy-first approach to information security, malware prevention and detection strategies, stolen or lost device or records protection, and emerging technologies.
As technology evolves, so do cybercriminals’ tactics—making staying ahead of them more crucial than ever. Organizations must be aware of current cybersecurity trends as well as prepare for future ones in order to stay secure. This article will provide an overview of what to expect when it comes to cybersecurity trends in 2023.
Identifying Cyber Threats
Identifying cyber threats is an essential part of protecting your business from cyber-attacks. Cyber threats can be classified into two categories: malicious and non-malicious. Malicious threats are those that are intended to harm or steal data, while non-malicious threats are those that occur naturally, such as viruses and malware.
The first step in identifying cyber threats is to understand the different types of attacks that exist. Common malicious cyber threats include phishing, ransomware, denial of service (DDoS), and distributed denial of service (DDOS). Phishing involves sending emails or messages with malicious content in order to lure people into clicking on malicious links or downloading malware. Ransomware is a type of malware that encrypts files until a ransom is paid. DDoS and DDOS attacks involve flooding a website or network with requests in order to overwhelm it with traffic and cause it to crash.
In addition to understanding the different types of cyber threats, one should also be aware of how they can be identified. Signs that you may have been targeted by a malicious attack include strange emails from unknown senders, unexpected pop-ups on your computer screen, slow performance from your computer or internet connection, and changes made to software/apps installed on your device without permission.
To protect yourself from cyberattacks it’s important to use strong passwords for all accounts and devices; regularly update software/apps; avoid clicking suspicious links; never download anything without verifying its source; back up important data regularly; and use multi-factor authentication when available. By taking these steps you can help protect yourself against identity theft and other online scams.

Cloud Security
Cloud security is the practice of protecting data and systems stored on cloud computing environments. It involves a range of processes, tools, and technologies designed to protect data from unauthorized access, cyber-attacks, and other malicious activities. Cloud security requires a comprehensive approach that includes authentication, authorization, encryption, access control, monitoring, auditing and compliance.
Cloud security solutions help organizations protect their data from unauthorized access by using powerful encryption algorithms that are difficult for attackers to break. They also provide secure networks with firewalls that can detect and block malicious traffic. Additionally, they monitor user activity on the cloud to ensure that only authorized users have access to sensitive information.
Organizations should also be aware of potential risks associated with cloud storage such as data leakage or accidental loss of information due to human error or hardware failure. To mitigate these risks they should deploy robust backup solutions and regularly audit their systems for any potential vulnerabilities or threats. Organizations should also ensure compliance with relevant legal requirements related to data privacy and cybersecurity.
Overall, implementing effective cloud security measures is essential for businesses in order to keep their digital assets safe against cyber threats in the ever-evolving digital landscape.
Automation in Security Solutions
Security solutions are becoming increasingly automated and sophisticated, allowing businesses to protect their data and assets more effectively than ever before. Automation in security solutions provides organizations with an efficient way to identify, respond to, and mitigate threats quickly. Automation also helps reduce costs associated with manual processes.
Automated security solutions enable businesses to detect malicious activity faster, while also reducing the amount of work required from security teams. Automation can help with threat detection by monitoring network traffic for indicators of compromise (IoC) or malicious activities such as malware or ransomware. Security teams can then take action quickly when a threat is identified, such as isolating affected devices or networks and mitigating the risk of further damage.
AI is often used in automated security solutions to identify patterns in large datasets that would be impossible for humans to detect manually. AI-based security solutions are able to learn from past incidents and use this knowledge to better protect against future threats, making them more accurate over time. AI-based solutions can also provide valuable insights into potential risks so that businesses can take proactive measures before an attack even occurs.
Automated security solutions are becoming essential for businesses as cybercriminals become increasingly sophisticated in their tactics and the number of threats continues to grow exponentially every year. By using automated security measures, organizations can be better prepared for any type of attack and respond quicker when necessary.
AI and Machine Learning for Cybersecurity
AI and machine learning are revolutionizing the way we approach cybersecurity. With advancements in artificial intelligence, automated systems can detect threats faster than ever before and can protect networks from malicious attacks. AI and machine learning algorithms can analyze vast amounts of data to identify patterns that may indicate a potential attack or suspicious activity, allowing organizations to respond quickly before any damage is done.
Additionally, AI and machine learning are being used to automate many of the tedious tasks associated with cybersecurity, freeing up staff to focus on more complex tasks. As these technologies continue to evolve over the next few years, they will become increasingly essential for keeping our digital world safe.

Passwordless Authentication
Passwordless authentication is an innovative form of cybersecurity that is quickly becoming a popular trend in the digital world. It eliminates the need for users to remember complex passwords by relying on other forms of identity verification, such as biometrics or one-time codes. This type of authentication has many benefits, including improved security and user convenience.
The traditional password system relies on users remembering and using a complex combination of letters, numbers, and characters to gain access to their accounts. Unfortunately, this system can be vulnerable to hackers who use sophisticated methods to crack passwords easily. Passwordless authentication provides an additional layer of security by making it harder for cybercriminals to gain access to accounts.
In addition to improved security, passwordless authentication also provides users with greater convenience since they don’t have to remember complex passwords or regularly change them due to fear of being hacked. This type of authentication also allows users more flexibility when it comes to logging in because they can use a variety of methods such as biometrics, one-time codes sent via text message or email, or even facial recognition software.
As technology advances and the demand for better security grows, more companies and organizations are beginning to embrace passwordless authentication as an alternative means of protecting user data from cyber threats. As this trend continues into 2023 we will likely see more businesses adopting passwordless authentication solutions as part of their overall cybersecurity strategy.

Exploring Blockchain Technology
Exploring Blockchain Technology is quickly becoming a top priority for businesses of all sizes as the technology has the potential to revolutionize how we store and share data. Blockchain is essentially a distributed digital ledger that records and stores transaction data in an immutable and secure way. By using cryptography, blockchain ensures that no-one can manipulate or alter information without permission from the other participants in the network.
The implications of blockchain technology are vast, with its potential applications ranging from financial services to healthcare, supply chain management, smart contracts, digital identity management, and more. Companies across multiple industries have been exploring how they can use blockchain to improve their operations and create new opportunities for growth.
For example, banks have been exploring how they can utilize blockchain technology to reduce costs associated with processing payments while improving security features and ensuring customer data privacy. Healthcare organizations are also beginning to explore how they can leverage blockchain to securely store patient records while maintaining privacy standards such as HIPAA compliance. Additionally, companies are looking into ways they can use smart contracts with blockchain technology to automate transactions and optimize their operations further.
As companies continue to explore the uses of this technology, it’s important that they understand the benefits and risks associated with implementing a blockchain solution before proceeding further down the path of development. By understanding these risks now, businesses will be better prepared for success when utilizing this powerful technology in 2023 and beyond.
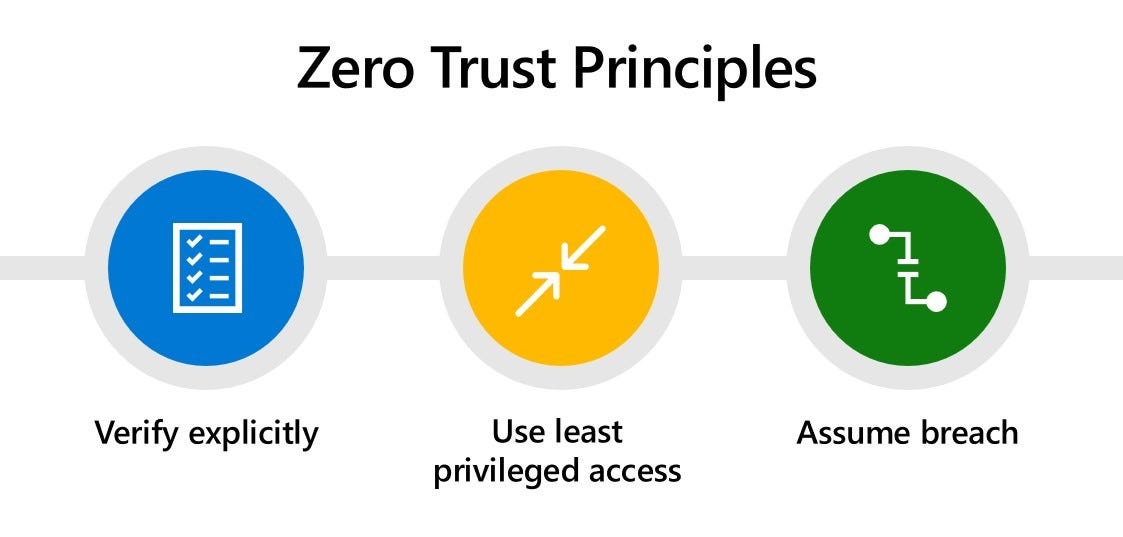
Zero Trust Model of Security
Zero Trust Model of Security is a security system that focuses on authentication, verification, and monitoring of users, devices, data access and network connections. It is designed to protect against sophisticated cyber threats by creating multiple layers of security that must be continually monitored and updated. Zero Trust Model works by continuously verifying the identity of users, suppliers and customers in order to limit access to only those with valid credentials. It also restricts what parts of the system each user can access and monitors their activities closely.
The idea behind Zero Trust Model is that no one should automatically be trusted without first being authenticated and validated. This includes internal users as well as external ones such as customers or partners. Furthermore, all network traffic must be inspected for malicious activity before it is allowed access to the system’s resources.
By implementing a Zero Trust Model of Security, organizations can improve their overall security posture and reduce their risk from cyber threats. This type of model promotes an environment where users are regularly monitored for suspicious activity, unauthorized access attempts are blocked quickly, and data leakage is prevented at all levels. Additionally, it helps organizations maintain compliance with relevant regulations such as GDPR or HIPAA by ensuring that proper safeguards are in place to protect sensitive data from misuse or theft.

Multi Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is an essential security measure that provides additional layers of protection for users and businesses. MFA requires two or more authentication factors, such as a password, biometric scan, or physical token, to gain access to a system. This added layer of security increases the difficulty for attackers trying to gain unauthorized access to sensitive data.
Businesses are increasingly adopting MFA due to its ability to reduce the risk of identity theft and fraud. By using multiple authentication methods, users can have confidence that their accounts are more secure from potential attackers. With MFA in place, organizations can also be sure that only authorized personnel will be able to access important systems and data.
MFA is becoming increasingly popular as businesses become more aware of the risks associated with traditional username/password combinations. It also allows businesses to easily manage user access rights across multiple platforms while reducing the chances of unauthorized access attempts. As technology continues to evolve so too will MFA solutions, making them even more secure and reliable in the future.

Increased Focus on Endpoint Security
Endpoint security is an important aspect of cybersecurity, and it has become increasingly important in recent years. Endpoints are the nodes or devices that access a network, such as computers, phones, tablets, and other internet-connected devices. These endpoints can be vulnerable to cyber threats if not properly secured.
In 2023, businesses should expect increased focus on endpoint security as cybercriminals become more sophisticated in their tactics and target these endpoints for exploitation. To protect endpoints from malicious software and other threats, organizations should implement robust endpoint security solutions that include antivirus software, firewalls, encryption technology, identity management systems and more. Additionally, businesses should educate users on best practices for securely accessing company networks via their personal devices to ensure that all confidential data is protected.
By investing in quality endpoint security solutions and educating users on secure network access practices now, organizations can reduce their risk of a data breach or system outage due to malicious activity in the future.

Protecting Internet of Things (IoT) Devices
As the number of Internet of Things (IoT) devices continues to grow, so does the need for security. Protecting these devices from cyberattacks is of utmost importance to ensure data is kept safe. IoT devices are vulnerable to being hacked and can be used to access sensitive information such as personal data or confidential business information.
There are various measures that can be taken in order to protect IoT devices from these kinds of cyber threats. One way is through secure authentication, which requires users to enter a unique password or code before being granted access. Another method is encryption, which scrambles data so it cannot be read by anyone other than the intended recipient. Additionally, regular software updates should be applied in order to ensure that any security vulnerabilities are patched as soon as possible.
It’s also important for organizations using IoT devices to have an effective incident response plan in place in case an attack occurs. This should include steps such as isolating affected systems and conducting an investigation into what happened and how it was prevented in the future. Organizations should also consider investing in cybersecurity insurance, which can help cover costs related to a breach or attack on their systems.
By taking these measures, organizations can better protect their IoT devices from cyberattacks and prevent sensitive data from falling into the wrong hands.
Data Protection Regulations
Data protection regulations are laws that protect the privacy and security of personal information. They ensure that businesses and organizations handle data responsibly by following best practices and avoiding misuse or unauthorized access. By setting out clear requirements for how data is collected, stored, shared, and used, these regulations help protect the rights of individuals while enabling organizations to use data in ways that benefit society. Companies must comply with these regulations or face fines, legal action, or other consequences. Data protection regulations are essential for protecting people’s privacy and creating trust in digital systems.

Securing Mobile Applications
Securing mobile applications is an increasingly important topic in the world of cybersecurity. With more people using mobile devices to access the internet, it’s important to ensure that these applications are secure from malicious activities such as malware, data theft, and hacking. To do this, organizations need to develop and implement effective security measures that can protect their users’ data and privacy. This may include encryption technologies, two-factor authentication (2FA), firewalls, and other security programs.
Additionally, organizations should also consider implementing secure coding practices for mobile application development, which will help to prevent any vulnerabilities from being exploited by attackers. Finally, regular maintenance of these applications is essential in order to maintain a secure environment for users. By following these best practices, organizations can ensure that their mobile applications remain secure and protected from potential threats.
Cloud Access Security Brokers (CASB)
Cloud Access Security Brokers (CASB) are an important part of any enterprise’s security strategy. CASBs provide a layer of protection between cloud services and enterprise systems, helping to ensure data is secure and access is properly managed.
CASBs are designed to monitor, control, and protect cloud-based applications from malicious threats, unauthorized access, and policy violations. They offer a range of capabilities such as identity management, access control & authorization, data encryption & masking, and threat detection & response.
By 2024 it is expected that 30% of enterprises will deploy Cloud Access Security Brokers (CASB) technology as part of their overall digital transformation initiatives. This will give them the ability to better manage their security posture in the cloud. CASB solutions also allow organizations to quickly detect suspicious activity in their environment, respond quickly with automated remediation actions or even block malicious traffic entirely.
In addition to protecting against threats, Cloud Access Security Brokers can also help organizations comply with industry regulations such as GDPR or HIPAA. By automating policy enforcement across all cloud services used by an organization they can ensure that all necessary measures are taken to protect sensitive customer data and reduce the risk of data breaches or other compliance violations.
Overall Cloud Access Security Brokers (CASB) are a critical component for any organization looking to maximize their security posture in the cloud-centric world we live in today.
Conclusion
Conclusion – Cybersecurity is a fast-evolving area and the threat landscape will continue to be an ever-present concern for organizations in 2023. As digital transformation investments increase, user awareness is essential to ensure that businesses remain secure and protected from cybercrime. Automotive hacking, malware attacks (such as ransomware), and information-stealers are all threats that must be monitored. IT leaders should take preventive measures to ensure their supply chains are secure from cyber threats. With proper preparation and vigilance, organizations can stay ahead of the ever-changing threat landscape in 2023.



