In today’s world, more and more businesses are relying on digital systems and networks to operate. This reliance comes with increased risk, as these systems and networks are vulnerable to cyberattacks. A cyber incident is any event that compromises the confidentiality, integrity, or availability of an information system or the data it stores.
When a business suffers a cyber incident, it is important to respond quickly and effectively in order to minimize the damage. This article will provide best practices for a cyber incident response process, covering topics such as preparation, identification, containment, eradication, recovery, and lessons learned. By following these best practices, businesses can ensure that they are ready to handle a cyber incident should one occur.
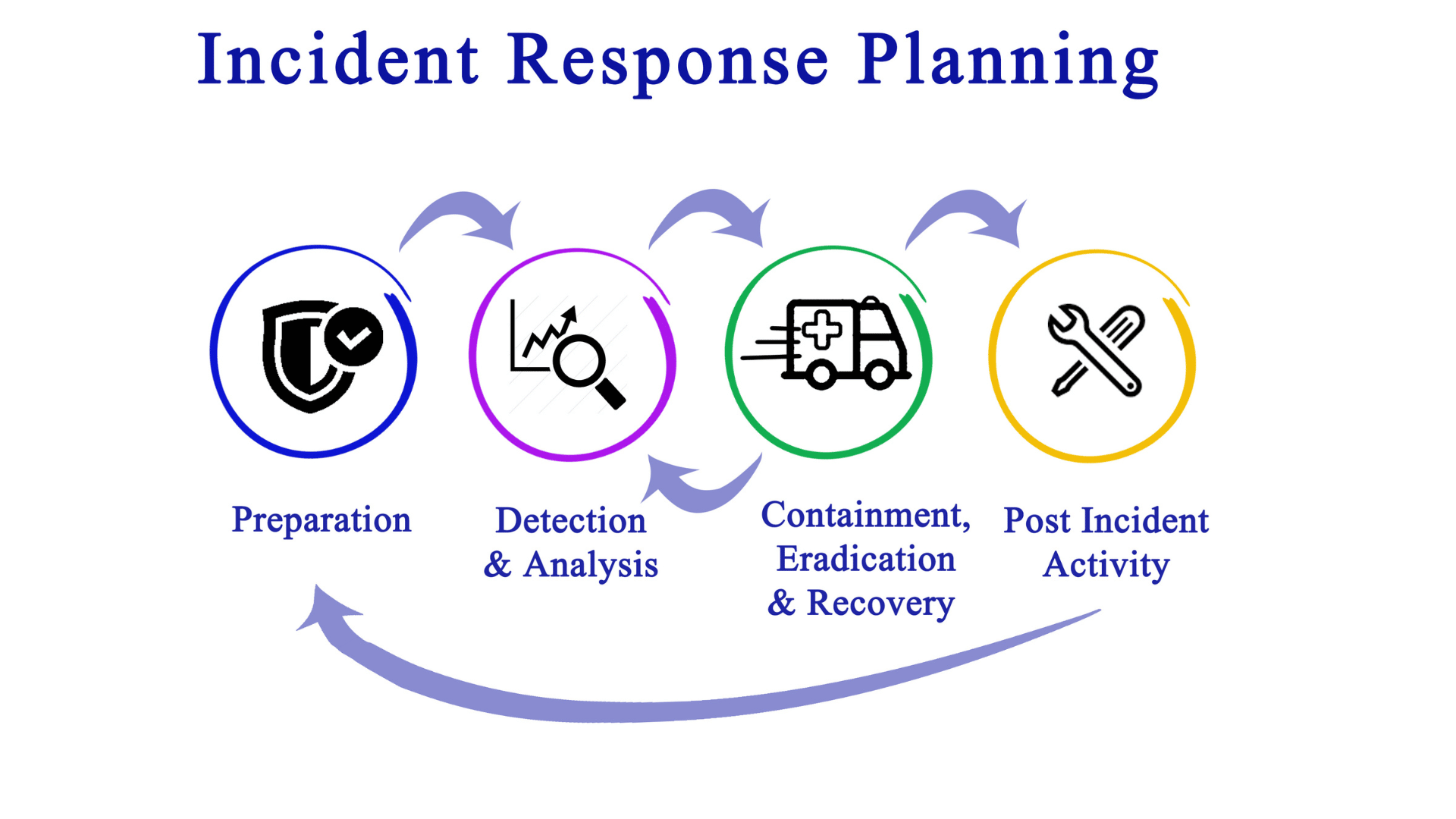
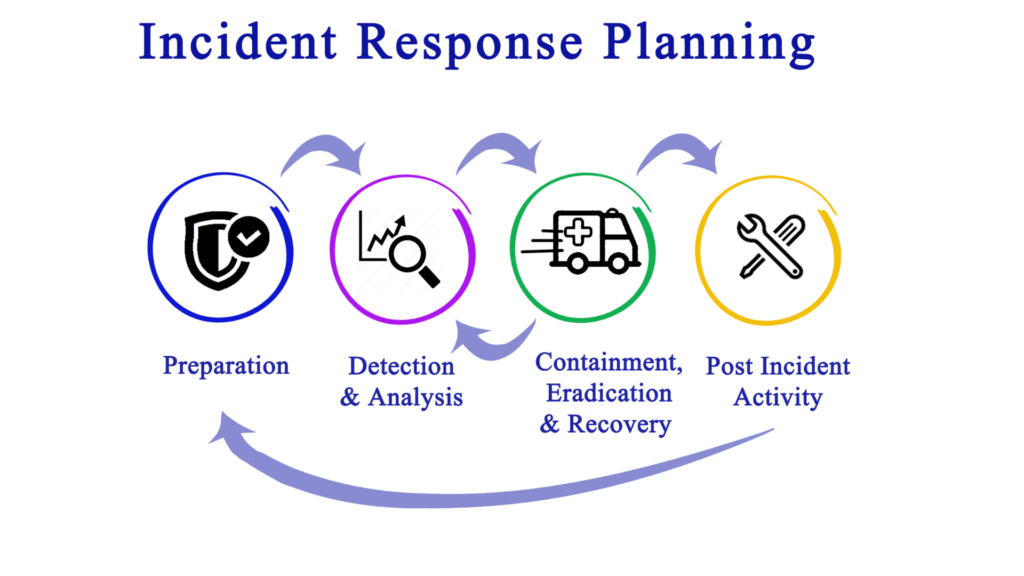
Preparation
In order to be prepared for a cyber incident, organizations should have a clear and well-documented incident response plan. The plan should be tailored to the organization’s specific needs and should be reviewed and updated on a regular basis. Prior to an incident, all staff should be aware of the plan and their roles and responsibilities within it.
The plan should be tested regularly to ensure that it is effective and that all staff are familiar with it. Organizations should also have a team of trained and experienced personnel who are responsible for coordinating the response to a cyber incident.
This team should have access to all the necessary resources and should be able to quickly mobilize in the event of an incident. In addition to having a solid cyber incident response plan, organizations should also make sure that they have up-to-date backups of all their critical data.
These backups should be stored in a secure location and should be regularly tested to ensure that they are working properly. Organizations should also implement security controls to help prevent cyber incidents from occurring in the first place. These controls should be reviewed and updated on a regular basis in order to keep up with changing threats.
Identification
The first step in any cyber incident response is identifying that a cybersecurity incident has occurred. This may seem like a no-brainer, but it’s actually one of the most difficult steps, as many times incidents go undetected for weeks, months, or even years. Identification can be difficult for a number of reasons, including the fact that not all incidents will generate obvious signs or a vulnerability in the system.
In fact, many incidents will go unnoticed by traditional security measures, such as intrusion detection systems (IDS) or firewalls. Instead, identification often requires a combination of people, processes, and technology working together to piece together various indicators of an attack.
One of the most important factors in successful incident identification is having a well-trained and dedicated incident response team. This team should be responsible for monitoring your organization’s networks and systems for signs of an attack, as well as investigating any potential incidents.
The team should also have a clear understanding of your organization’s normal baseline activity, so they can more easily identify unusual or suspicious activity. In addition to having a dedicated incident response team, it’s also important to have clear and concise policies and procedures in place for reporting and responding to incidents.
These policies and procedures should be regularly reviewed and updated by stakeholders to ensure they reflect the latest best practices.
Technology also plays an important role in incident identification. A variety of tools and platforms are available to help security professionals detect cyber incidents. These tools can range from simple log files to more sophisticated analytics platforms that use machine learning to detect anomalies. Security teams should leverage as many tools and technologies as possible to improve their chances of detecting an incident.
In summary, successful incident identification requires a combination of people, processes, and technology working together. Having a dedicated incident response team is critical, as is having clear policies and procedures in place for reporting and responding to incidents. Leveraging multiple tools and technologies will also improve your chances of detecting an incident.
Containment
As soon as an organization suspects or confirms that it has suffered a security incident, it should take steps to contain and limit the damage. The goal of containment a data breach is to stop the attack, limit its spread, and prevent further damage. There are a number of steps that can be taken to contain a cyber incident: –Isolate affected systems: Disconnect affected systems from the network and power them down if possible.
This will help to prevent the spread of malware and limit data loss. –Contain malware: Use anti-malware software to scan and remove malware from affected systems. –Restrict access: Limit access to systems and data that may have been compromised.
This includes changing passwords and revoking user access as needed. –Disable services: Disable any unnecessary services that may be running on affected systems. This will help to reduce the attack surface and limit the damage that can be done. –Monitor activity: Closely monitor system activity for signs of unusual or suspicious behavior. This includes monitoring logs, traffic, and user activity.
Eradication
Eradication is the process of removing the malicious code or activity from your systems and restoring normal operations. This can be a challenge, especially if you don’t know what you’re looking for or where it is. It’s also important to make sure that you don’t inadvertently delete or damage critical systems or data.
There are a few different approaches that can be taken when eradicating malware from a system: -Reformatting and reinstalling the operating system and all applications. This is a time-consuming process, but it guarantees that the malware is removed. -Using specialized malware removal tools.
These tools are designed to find the root cause and remove specific types of malware. Some are free, while others must be purchased. -Manually removing the malware. This can be difficult and time-consuming, but it may be possible to remove the malware without damaging critical systems or data. Once the malware has been removed, it’s important to take steps to prevent it from being reinstalled. This includes changing passwords, updating software, and running regular scans with antivirus and anti-malware tools.
Recovery
Recovery is the process of returning systems and data to a known, working state after a disruption. It may involve rebuilding lost data, reconfiguring systems, or restoring applications. The goal of recovery is to minimize downtime and data loss, and to ensure that systems are returned to a known good state as quickly as possible.
There are many factors to consider when planning for recovery, including: –RPO (recovery point objective): the maximum acceptable amount of data that can be lost in a disruption –RTO (recovery time objective): the maximum acceptable amount of time that systems can be down in a disruption -Business criticality: which systems and data are most critical to the operation of the business -Recovery strategies: which recovery strategies are most appropriate for each type of system or data There are several different types of recovery strategies, including: –Full backup: all systems and data are backed up on a regular basis, typically nightly. In the event of a disruption, all lost data can be restored from the most recent backup.
This strategy is typically used for mission critical systems where data loss is not acceptable. –Incremental backup: all systems and data are backed up on a regular basis, but only changes since the last backup are stored. In the event of a disruption, lost data can be restored from the most recent backup plus any incremental backups that have been made since then.
This strategy is typically used for less critical systems where some data loss is acceptable. –Differential backup: all systems and data are backed up on a regular basis, but only changes since the last full backup are stored. In the event of a disruption, lost data can be restored from the most recent full backup plus any differential backups that have been made since then.
This strategy is typically used for less critical systems where some data loss is acceptable. –Snapshot: periodic copies of all systems and data are stored, typically at intervals of hours or days. In the event of a disruption, lost data can be restored from the most recent snapshot. This strategy is typically used for less critical systems where some data loss is acceptable.
Lessons Learned
There are a number of important lessons that can be learned from recent large-scale cyber incidents. These lessons can help organizations to improve their own incident response plans and practices.
1. The importance of having a plan: Organizations that have a well-documented and tested incident response plan are generally better prepared to deal with a major incident. This was clearly demonstrated in the wake of the WannaCry ransomware attack, where those organizations that had a plan in place were able to respond more quickly and effectively than those that didn’t.
2. The importance of training: Incident response plans are only effective if they are understood by those who need to use them. Training is therefore essential, both in terms of familiarizing staff with the plan itself, and in terms of ensuring that they have the skills and knowledge required to implement it effectively.
3. The importance of communication: In any major incident, communication is key. This includes both internal communication (ensuring that all relevant staff are kept up to date with developments) and external communication (such as dealing with the media).
4. The importance of collaboration: Cyber incidents often require a collaborative response from multiple organizations, both within the affected organization and outside of it. Incident response plans should therefore include provisions for collaboration, both in terms of formal arrangements with other organizations and in terms of more informal information sharing.
5. The importance of documentation: Documentation is vital for two main reasons: first, as a record of what happened during an incident (which can be used to improve future responses); and second, as evidence if legal action is required.
6. The importance of review: Once an incident has been resolved, it’s important to take some time to review what happened and identify any improvements that could be made to the organization’s incident response plan or practices.
7. The importance of continually improving: Given the ever-changing nature of the threat landscape, it’s important for organizations to continually review and update their incident response plans and practices. What might have been an effective response to a particular threat today might not be effective tomorrow, so it’s important to keep up with the latest changes and trends.
What should a cyber incident response plan include?
At a minimum, a cyber incident response plan should include:
1. A clear and concise statement of the organization’s overall incident response philosophy.
2. The roles and responsibilities of the incident response team members and other key stakeholders.
3. The processes and procedures for detecting, investigating, and responding to incidents.
4. The communication plans and procedures for alerting stakeholders and sharing information internally and externally.
5. The procedures for regularly testing and updating the incident response plan.
Why is cyber incident response important?
There are many reasons why cyber incident response is important. First, incident response can help an organization understand the scope and impact of a security incident. Additionally, incident response can help organizations contain and mitigate the incident, as well as reduce the likelihood of future incidents. Furthermore, incident response can help organizations recover from an incident and resume normal operations. Finally, incident response can help build organizational resilience and increase the overall security of the organization.
Conclusion
As the world becomes increasingly digitized, organizations must be prepared to face a growing number of cyber threats. An effective cyber incident response plan can mean the difference between a minor setback and a major disaster.
The best way to prepare for a cyber incident is to have a well-defined plan in place before an incident occurs. The plan should be reviewed and updated regularly to ensure that it remains relevant and effective.
Identification of a cyber incident is often the first step in the response process. It is important to have systems and processes in place to quickly and accurately identify incidents.
Once an incident has been identified, containment is the next step. Containment strategies should be designed to minimize the impact of an incident and prevent it from spreading.
Eradication of a cyber threat is the next goal in the response process. This may involve removing malicious code, repairing damaged systems, or taking other steps to neutralize the threat.
Recovery from a cyber incident can be a complex and time-consuming process. It is important to have a plan in place to ensure that systems and data are recovered quickly and effectively. You may have to rely on an external company to help with digital forensic to help prioritize and outline the steps it will take to get you back up and running.
Finally, it is important to learn from each cyber incident and use those lessons to improve future responses. By following these best practices, organizations can be better prepared to face the challenges of today’s digital world.