Our countries national and economic security relies on the resilience and functionality of critical infrastructure. Cyber crimes are a growing threat to the complexity and connectivity of our critical infrastructure systems, putting the Nation’s security, economy, and public safety and health at risk. Just like the risks of financial and reputation, cyber crimes affect the bottom line for company’s. It has the potential to increase cost, which has a huge impact on revenue. It can stop production and innovation, as well as affect the organization’s ability to gain and keep client.
In February 12, 2013 the President of the United States issued Executive Order 13636 “Improving Critical Infrastructure Cybersecurity,” “it is the Policy of the United States to enhance the security and resilience of the Nation’s critical infrastructure and to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity while promoting safety, security, business confidentiality, privacy, and civil liberties.” The main reason for this Executive Order is to call for the development of a voluntary risk-base Data Security best practice framework. This framework is designed to bring together the government and private sectors, with a single language to address and manage cyber risks. The structure of this framework is designed to be a cost-effective way to support businesses without increased regulatory requirements.
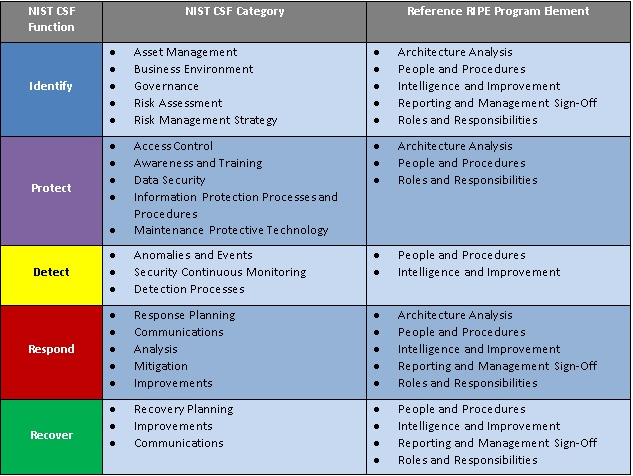
Here at Sentree Systems, we structure our security practice around the framework designed by NIST (National Institute of Standards and Technology). Their framework if the CSF (Cyber Security Framework).
The Framework focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes. The Framework consists of three parts: the Framework Core, the Framework Profile, and the Framework Implementation Tiers. The Framework Core is a set of cybersecurity activities, outcomes, and informative references that are common across critical infrastructure sectors, providing the detailed guidance for developing individual organizational Profiles. Through use of the Profiles, the Framework will help the organization align its cybersecurity activities with its business requirements, risk tolerances, and resources. The Tiers provide a mechanism for organizations to view and understand the characteristics of their approach to managing cybersecurity risk.
To receive a certificate from Sentree Systems, Corp. your organization must be able to prove that you are in control of these areas presented in the framework. Once all steps are complete you will receive a certificate with you organizations name in it as well as a seal to place on your site.